5 minutes
Terraform Modules - Demo VPC in AWS
Context
While working with various clients, I like to experiment different infrastructure deployment depending on their requirements. It very often (if not, most of the time) requires a simple VPC with public and private subnets. The infrastructure being the same each times, I wanted to set up a basic terraform module to be able to re-use it whenever I needed.
I therefore took this opportunity to start a new post series for demonstrating how I set up new terraform projects using terraform modules, starting with a VPC including the NAT and internet gateway for the public subnet.
Terraform Modules
Modules can be defined as a generic and re-useable partial infrastructure. It can have a similar folder structure of a normal Terraform structure but it’s good practice to stick to specific one, to keep all modules as consistent as possible.
The way I’m describing here is only a simplistic and exemplary way that I personally prefer and wants to share. You are, of course, free to use it based on any requirements that you have.
Diving in
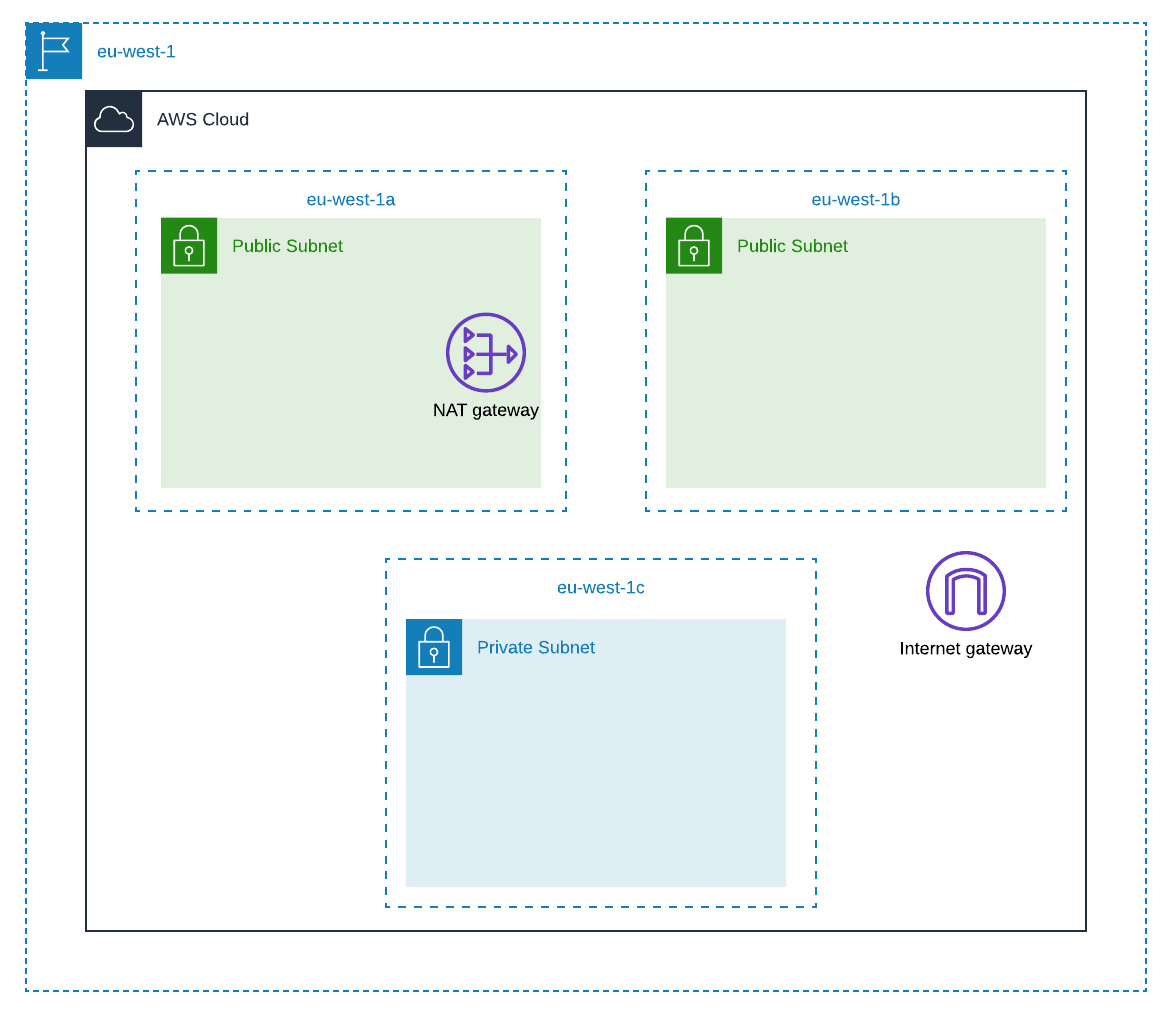
I’ll initially start with an architecture like this :
In our new repository, the list of files will be consisting of :
.
├── README.md
├── main.tf
├── outputs.tf
└── variables.tf
Defining variables
To make sure that modules are easy to use, I find it logical to provide a list of default values for as much of the variables as possible. All resources being created in the module should be using variables so that it can be flexible for the user to use.
| Name | Type | Default | Required |
|---|---|---|---|
| internet_gateway_name | string | “pasc-tech-demo-ig” | no |
| my_ip | string | n/a | yes |
| nat_gateway_name | string | “NAT-GW” | no |
| private_subnets | map | { “eu-west-1c”: “3”} | no |
| public_subnets | map | { “eu-west-1a”: “1”, “eu-west-1b”: “2”} | no |
| vpc_cidr | string | “192.168.0.0/16” | no |
| vpc_name | string | “pasc-tech-demo-vpc” | no |
Inside the variables.tf file, you would define variables as below :
[...]
variable "internet_gateway_name" {
type = string
default = "pasc-tech-demo-ig"
description = "Name of the Internet Gateway"
}
variable "public_subnets" {
type = map
default = {
eu-west-1a = "1"
eu-west-1b = "2"
}
description = "Map of AZ for the public subnet"
}
[...]
Resources
We can now define all the necessary resources in the main.tf file. The module will allow us to deploy a new VPC in a specific region. Taking example (default values) in eu-west-1 which has 3 availability zone, we’ll deploy 2 public subnet (eu-west-1a and eu-west-1b )and 1 private subnet (eu-west-1c).
The first public subnet will host the NAT gateway which will allow instances from the private subnet to connect to the internet, through the Internet Gateway.
Most of the resources a straight forward to build. The interesting part here is building new subnets based on the provided availability zones. Providing a map for each of them, we can loop the creation of the subnet by using the for_each function of Terraform.
For example, creating our 2 public subnets will look something like this :
[...]
# SUBNETS
resource "aws_subnet" "public_subnets" {
for_each = var.public_subnets
vpc_id = aws_vpc.main_vpc.id
cidr_block = cidrsubnet(aws_vpc.main_vpc.cidr_block, 8, each.value)
availability_zone = each.key
tags = {
Name = "public_subnet_${each.value}"
}
}
[...]
Routes
We’ll need to define the connectivity between the different component necessary for this basic VPC. Now that we have created both the NAT gateway and the Internet Gateway, you can define who is allowed to send traffic to and from the public and private subnets. For this demo, I’ve kept it as simple as possible :
- allow all traffic to/from the public subnet to the
Internet Gateway - all traffic from the private subnet goes to the
NAT gatewayonly. - allow traffic to/from my working laptop IP address to/from the private subnet
I’ve added my ip address mostly for debug and demonstration purposes. Obviously, this should not be deployed in a production environment.
First thing to do is to create 2 different route table, and set our required routes in it.
[...]
# ROUTE TABLE - towards internet gateway
resource "aws_route_table" "internet_route_table" {
vpc_id = aws_vpc.main_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "internet-route-table"
}
}
# ROUTE TABLE - towards NAT Gateway
resource "aws_route_table" "nat_route_table" {
vpc_id = aws_vpc.main_vpc.id
route {
cidr_block = var.my_ip
gateway_id = aws_internet_gateway.gw.id
}
route {
cidr_block = "0.0.0.0/0"
nat_gateway_id = aws_nat_gateway.nat_gw.id
}
tags = {
Name = "nat-route-table"
}
}
[...]
Next, we’ll associate these route table to their respective subnets :
# ASSOCIATE ROUTE TABLE -- PUBLIC subnet
resource "aws_route_table_association" "internet_route_table_association_app" {
for_each = var.public_subnets
subnet_id = aws_subnet.public_subnets[each.key].id
route_table_id = aws_route_table.internet_route_table.id
}
# ASSOCIATE ROUTE TABLE -- PRIVATE subnet
resource "aws_route_table_association" "nat_route_table_association_app" {
for_each = var.private_subnets
subnet_id = aws_subnet.private_subnets[each.key].id
route_table_id = aws_route_table.nat_route_table.id
}
Outputs
Terraform modules are good for isolating resources for one specific need but sometimes references to these resources might be required for later use. One easy way (of many) to help others or yourself in developing other modules, is to provide references to some or all of your resources using outputs.
For our example, we should be providing the VPC_ID from the outputs.tf file like this :
output "vpc_id" {
value = aws_vpc.main_vpc.id
description = "Created VPC ID"
}
The syntax for outputing a list of values is different from terraform v0.12+, here’s an example for the list of Private Subnet IDs :
output "private_subnet_ids" {
value = [
for subnet in tolist(aws_subnet.private_subnets.*)[0] :
subnet.id
]
description = "List of private subnet IDS"
}
Conclusion
We’ve seen how building a VPC in terraform can be structured using a simple module. It can be used for a quick PoC deployment, as part of a demo or for practice and understanding of how it all works. Next step is to demonstrate how to actually use this module within a simple Terraform project.
952 Words
26-04-2020 23:00